Take the next step
Talk to us today
The asset discovery tool, runZero (formerly Rumble), allows users to configure authenticated scanning, such as SNMP and VMWare. If not configured correctly, attackers can capture these credentials during a scan and use them to gain sensitive information about the network.
Authored by Stephen Shkardoon
Published on
runZero is a network discovery and asset inventory platform that uncovers every network in use and identifies every device connected–without credentials.
ZX Security purchased and has been using runZero (formerly known as Rumble) on engagements as an alternative to managing large results from Nmap for a long while now. While not its primary purpose, this allows us to get information back from port scans (as well as other discovery protocols that runZero supports) quickly and into a central location. However, we noticed while using it that the authenticated scanning, which supports many different protocols, is very easy to configure in such a way that rogue or malicious listeners can capture credentials. As a result, if we perform testing on a network that is using runZero, we’re able to capture the credentials that the instance is using for scanning.
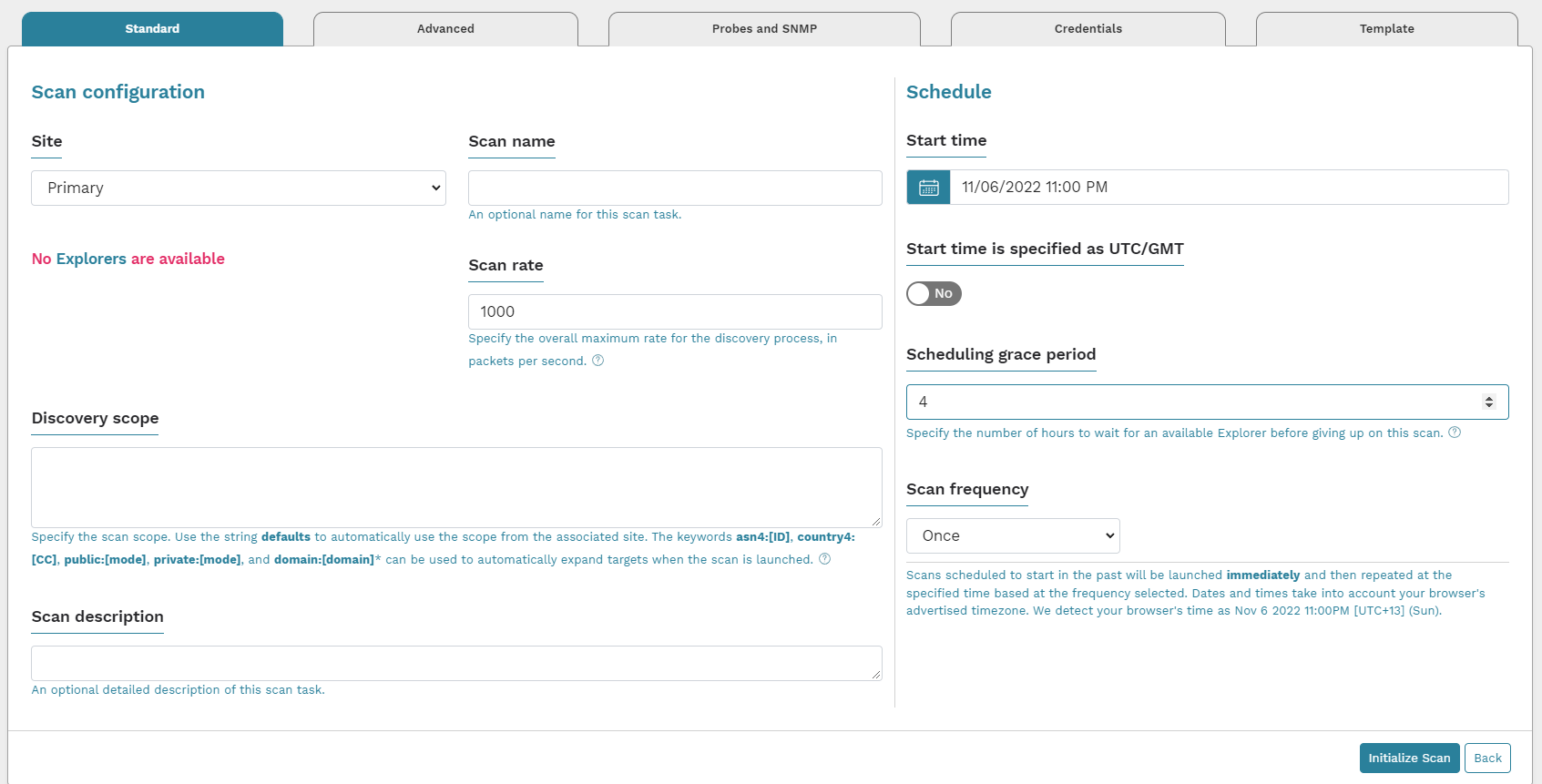 When you run a scan with runZero, you’re given most of the options you need right away. In our case, we’re interested in Credentials and how they work. You can either configure Credentials on a scan basis or add them to the organisation so they can be reused for multiple scans. In either case, you’re given a range of types of credentials that can be used, and more are added all the time. For this post, we’re going to focus on two types that are representative of the issue we’ve noticed, though the discussion applies to most of them.
When you run a scan with runZero, you’re given most of the options you need right away. In our case, we’re interested in Credentials and how they work. You can either configure Credentials on a scan basis or add them to the organisation so they can be reused for multiple scans. In either case, you’re given a range of types of credentials that can be used, and more are added all the time. For this post, we’re going to focus on two types that are representative of the issue we’ve noticed, though the discussion applies to most of them.
SNMPv2c and SNMPv1 are both protocols that we can trivially capture credentials for if they are sent to us. Because there’s no mutual authentication taking place, it’s not possible to ensure the IP you send the packet to is whom you are expecting, even if you wanted to. The exception to this is you can manually specify the IP addresses you wish to target with a given credential in runZero. As described in the runZero manual:
By entering your community strings as credentials, you can use the CIDR allow list feature to control which parts of the network the community strings will be sent to, reducing the risk of their being captured by rogue devices
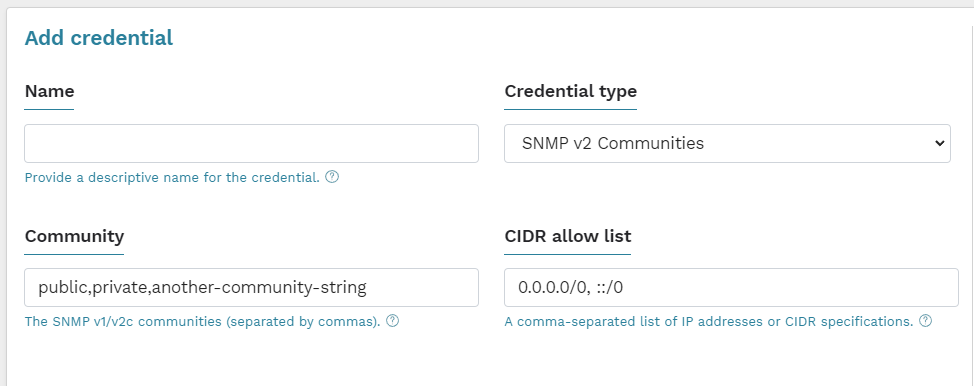
If someone configures this option without a CIDR specification to stop us, we’re able to get these credentials with any SNMPv2 listener, such as Responder. While Responder didn’t originally support capturing SNMPv2 credentials, this was easily added with a simple pull request to the main repository. Another option is to use a tool like Flamingo, which is able to capture a wider range of credentials and is specifically designed for this purpose.
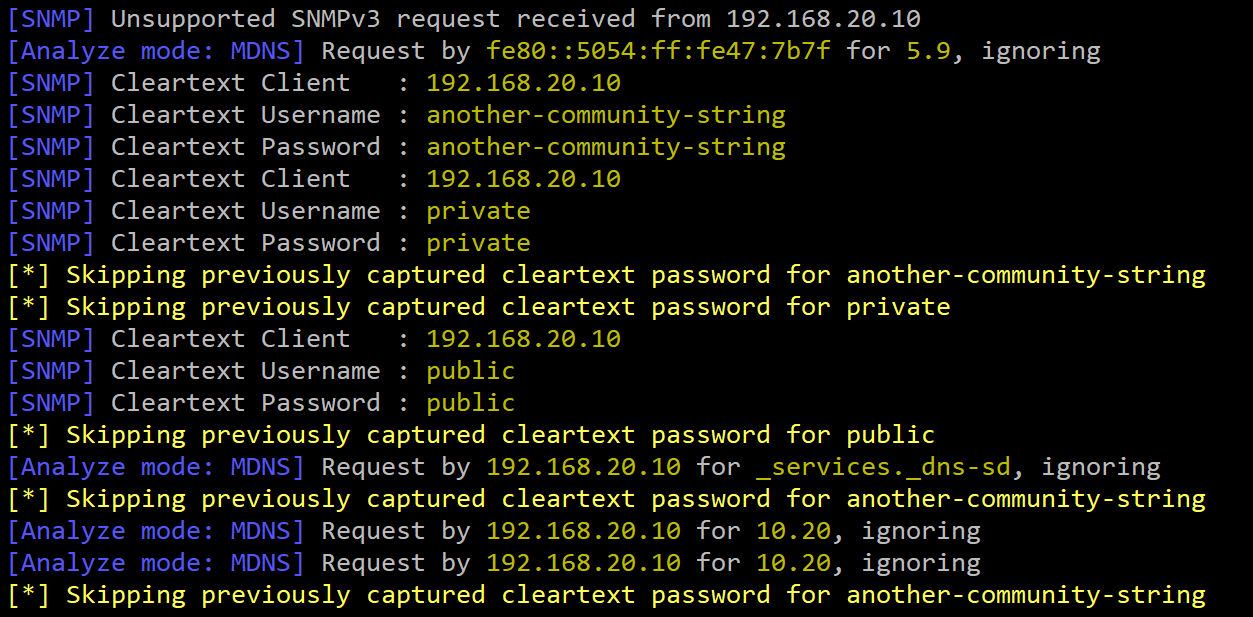
While Responder doesn’t support SNMPv3 yet, it is possible for an attacker to capture packets from SNMPv3 and perform an offline brute-force against the Authentication and Privacy passphrases (depending on how runZero has been configured).
runZero also supports talking to your VMware vCenter/ESXi instances and populating results that way. In contrast to SNMP, there is an additional way to verify the servers the scanner is authenticating to are legitimate: TLS certificates (specifically, their thumbprints).
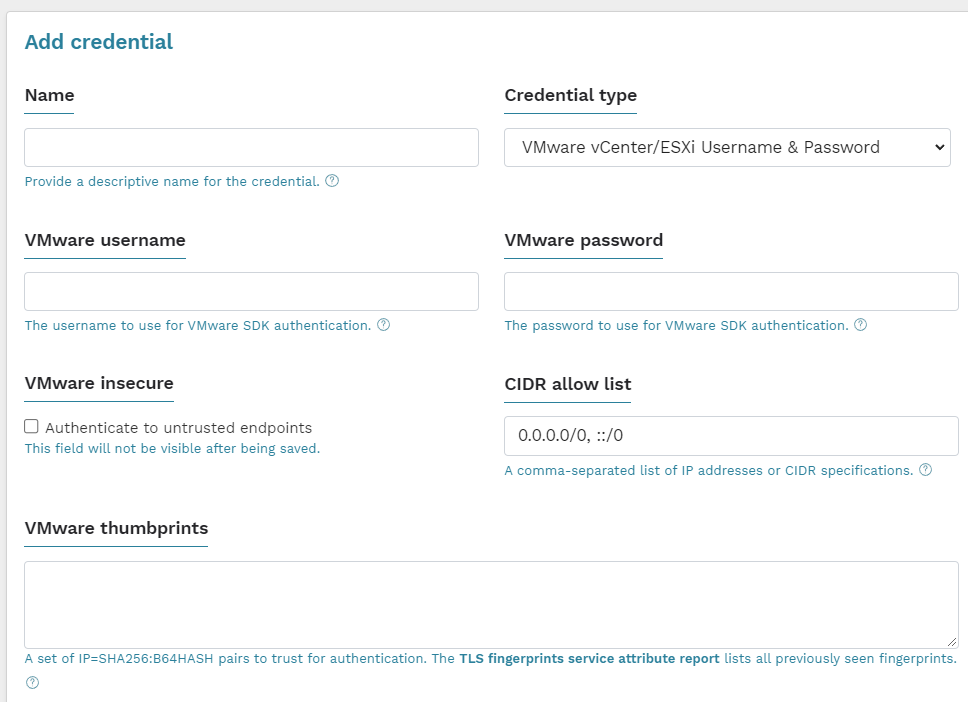 While this is secure, it seems unlikely that many people are using this list of TLS thumbprints to protect which servers they connect to. The good news is that as far as things look on Google, no one has written a listener that can capture the credentials of the scanner when attempting to authenticate with the VMware SDK.
While this is secure, it seems unlikely that many people are using this list of TLS thumbprints to protect which servers they connect to. The good news is that as far as things look on Google, no one has written a listener that can capture the credentials of the scanner when attempting to authenticate with the VMware SDK.
The impact of capturing credentials is very dependent on the situation, but in the experience of ZX Security, once you have one sensitive credential, be it SNMPv2 or any other, you can use it to gain further access to the environment. Often these credentials won’t be set up following best practice, and can be used as write community strings too, or can otherwise be reused against other systems.
It seems that while runZero has done a lot to help make sure users don’t configure these credentials insecurely, it is very easy to do so, especially in the case of SNMP. If you’re ever on a network and notice the runZero scanner (which is very easily identified based on the way it scans), run a listener for some of the scan types it can perform with credentials and hope you get lucky.
Talk to us today